A password is a key that provides access to something that is inaccessible without it. A form of authentication that uses secret data to control access to a resource. Thanks to passwords we can protect all our personal information and data stored on computers, cell phones and online accounts.
The use of passwords has been around since ancient times, from the early days of computing to the present day. In this post we tell you about the history and evolution of passwords and their use over the years.
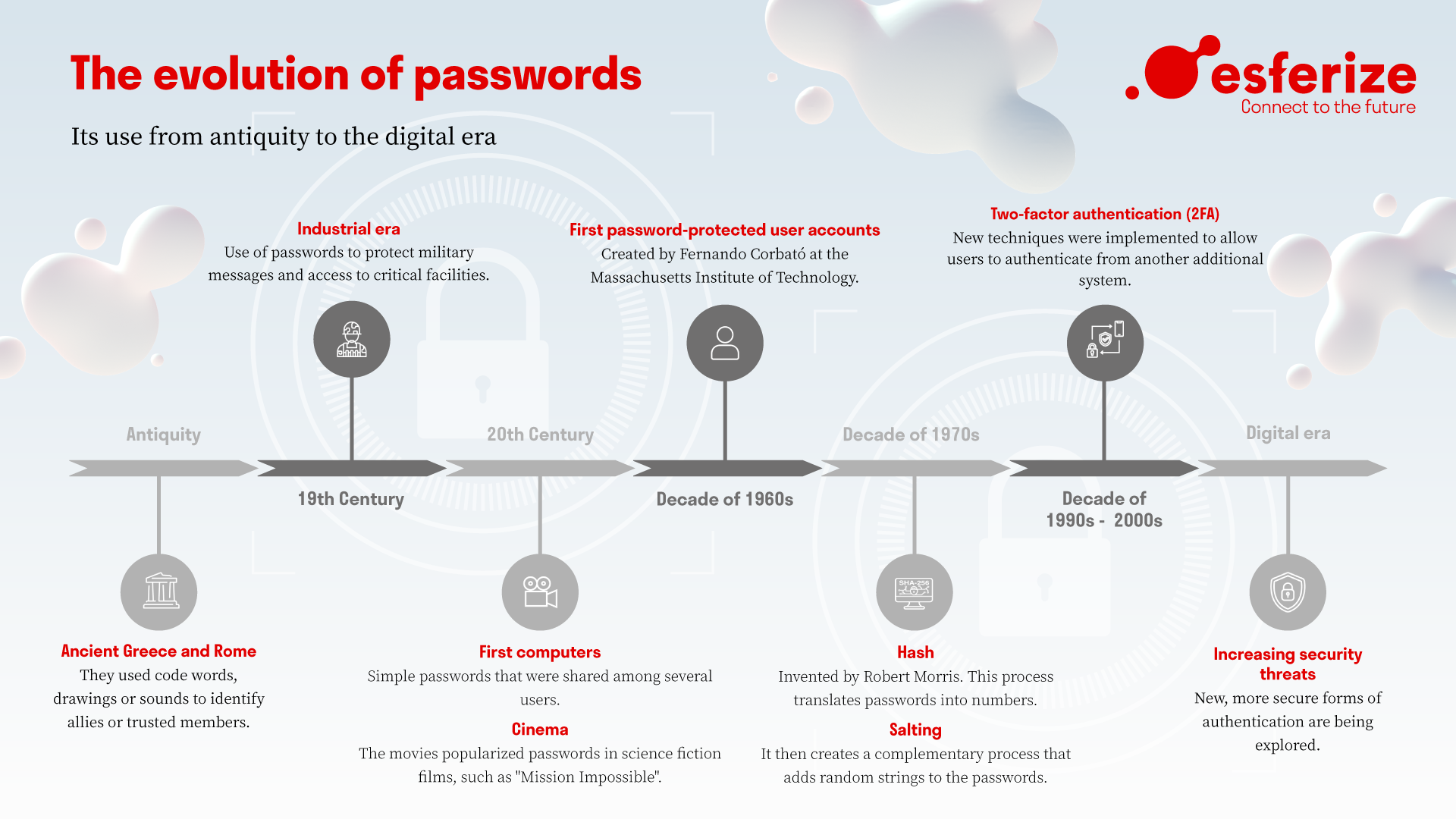
History and evolution of passwords
Passwords have been used throughout history as a way to protect sensitive information or restrict access to certain places or resources. Next, we will discuss the history and evolution of passwords and how they emerged from ancient times to the digital form we know today.
Antiquity
It is known that, since ancient times, in Ancient Greece, they used code words, drawings or sounds as ” holy and sign ” to enter places or to be recognized as part of the group. Also, the Romans used passwords to identify friends and allies in the dark to avoid surprise attacks, to transmit important military messages between troops or to replace someone else on guard duty.
In past ages, many tribes and communities also used keys to identify trusted members.
19th Century
During the industrial era, passwords were used to protect messages</strong> containing military and government information, or to restrict access to critical facilities.
20th Century
With the advent of the first computers</strong>, passwords, which were <strong>simple</strong> and generally shared among several users, became a form of authentication in computer systems. No attention was paid to the security of passwords.
At the end of the 20th century, movies popularized the use of passwords in science fiction films such as in “Mission Impossible” (1996), where Ethan Hunt accesses the CIA terminal with the password “AW96B6”.

At least they used a password with letters and numbers.
Decade of 1960s
In the 1960s, Fernando Corbató created the first password-protected user accounts at the Massachusetts Institute of Technology (MIT). Each user could access his or her own files on consoles linked to the university’s main computer.
The password was used to keep individual files private so that each user could access their contents at the times that corresponded to them.
Decade of 1970s
In 1972, cryptographer Robert Morris invented the hash. Hashing is an encryption process that translates passwords into numbers.
Following this, Morris collaborated with Ken Thompson to create a complementary process called salting. Salting adds random strings to passwords to make them harder to hack.
Both processes are still in use today.
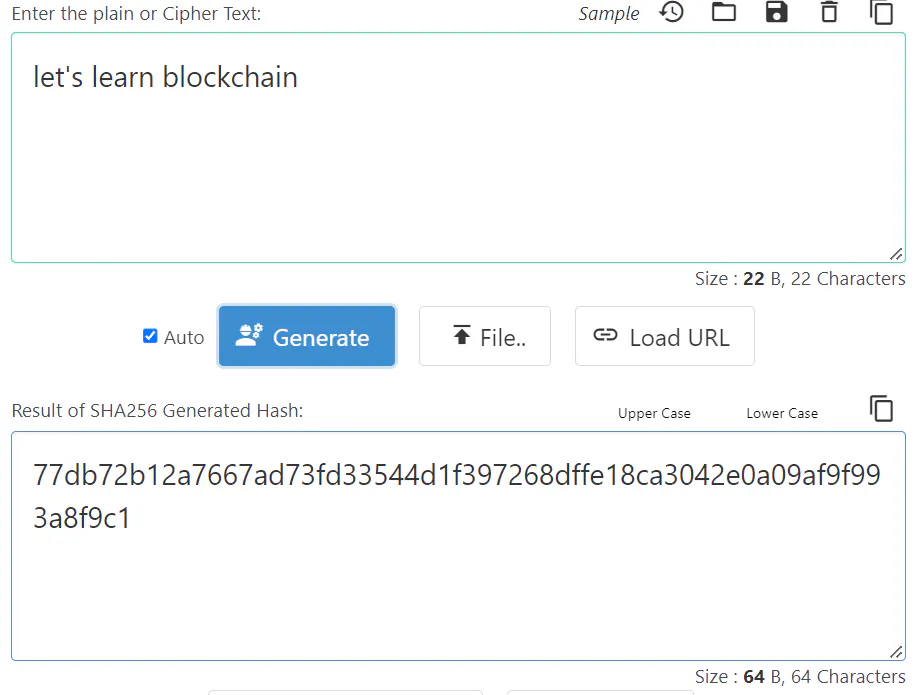
Example of Hash function
Decade of 1990s-2000s
With the growing threat of cyber attacks and online phishing, IT security has become a major concern. New techniques have been implemented such as longer passwords, two-factor and multi-factor authentication, use of password managers…
Two-factor authentication (2FA) is a very common system today. This system asks users to authenticate themselves through an additional system such as a temporary code in an SMS, an email or an authentication application.
As a result, companies allowed employees to use their private cell phones at work.
Digital era
Digital passwords have evolved to adapt to the growing security threats on the network, such as brute force attacks, phishing, identity theft, etc. Given these risks, new and more secure forms of authentication, such as biometrics and multi-factor authentication, are increasingly being explored.
Key tips for securing passwords
A strong password is the main barrier that prevents most of your online accounts from being hacked, so we want to share some key tips to ensure that all your passwords are as secure and resistant as possible to cyber threats:
- Avoid short passwords, try to keep them at least 10-12 characters long.
- Avoid predictable sequences of numbers and letters such as “1234” or “aabbcc”, also avoid common words such as “password”.
- Use combinations of lowercase, uppercase, symbols and numbers.
- Avoid obvious character substitutes, use the number “0” instead of the letter “O”.
- Use phrases that are meaningful to you and difficult for the computer to guess.
- Do not use passwords you already have on other accounts, create original passwords for each account.
- Do not share passwords through e-mail or messages.




